Our ISO 27001:2022 implementation experience was outstanding! Coral's team demonstrated exceptional expertise, guiding us through each step with clarity and expert advice. Their meticulous approach ensured full compliance with all requirements, and their ongoing support was invaluable. The project was completed on schedule and within budget, far surpassing our expectations. We now have complete confidence in our information security management system. I highly recommend their services for a smooth and professional implementation!
ISMS – ISO 27001 Consultant Engagement Phases
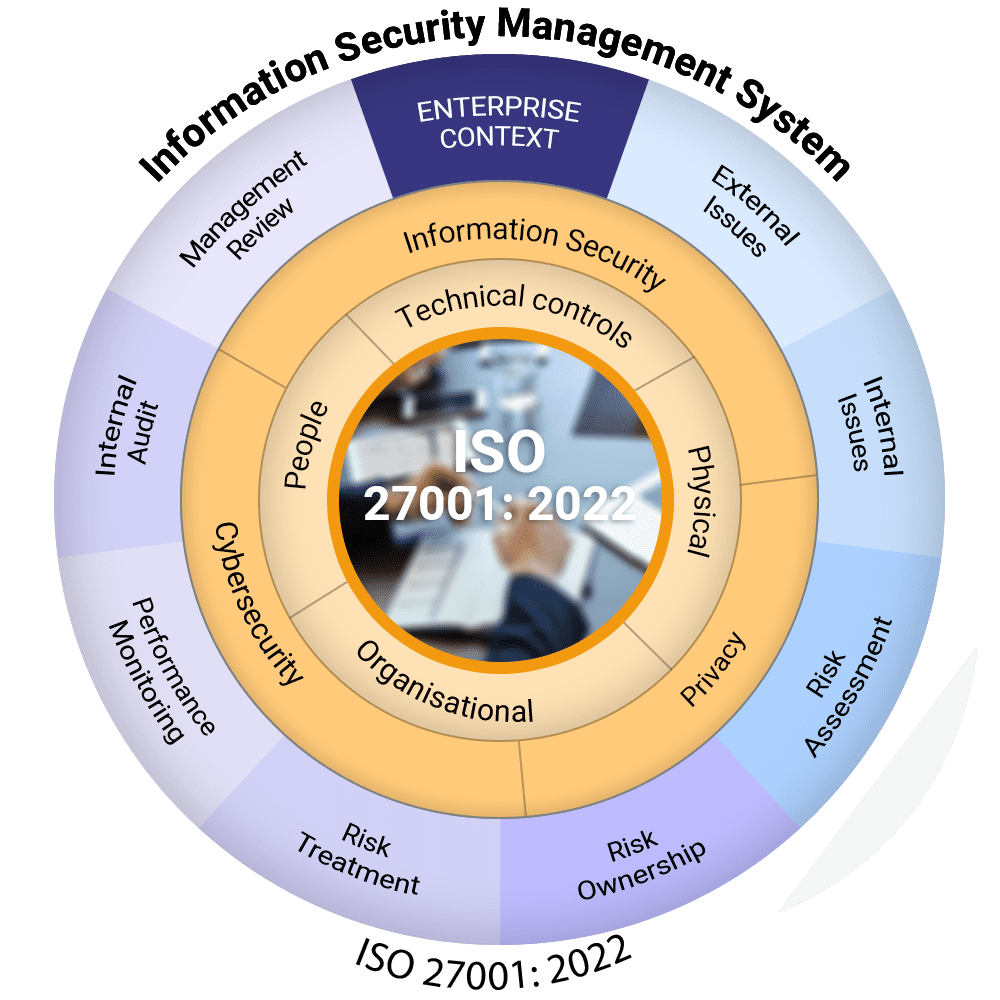
In today’s digital landscape, safeguarding your organization’s information is more crucial than ever. With the ever-increasing threats to data security, having a robust Information Security Management System (ISMS) in place is not just an option; it’s a necessity. Our ISO 27001 consulting services are designed to guide you through each vital phase of achieving compliance, ensuring your business objectives align with security goals. Our expert team is committed to transforming your approach to information security, protecting not only your data but also your reputation.
Key Phases of Our ISO 27001 Consulting Service

1. Understanding Business and Security Objectives
- Assessment of Current Landscape: We conduct a thorough evaluation of your existing security posture, identifying strengths and vulnerabilities.
- Aligning Security with Business Goals: Our consultants work closely with your team to ensure that security objectives support your overall business strategy.
- Stakeholder Engagement: We facilitate discussions with key stakeholders to understand their concerns and expectations, ensuring comprehensive buy-in.

2. Detail Gap Analysis and Risk Assessment
- Identifying Vulnerabilities: Our experts conduct a detailed gap analysis to uncover potential security weaknesses within your existing systems.
- Comprehensive Risk Assessment: We analyze risks to your information assets, considering both internal and external threats to create a complete risk profile.
- Prioritization of Risks: We help prioritize identified risks based on their potential impact and likelihood, guiding you in effective risk management.

3. Policy Documentation
- Development of Security Policies: We assist in drafting clear and effective information security policies tailored to your organization’s unique needs.
- Compliance Mapping: Our team ensures that all policies align with ISO 27001 requirements and best practices, ensuring compliance.
- Policy Training: We provide training sessions to ensure your staff understands and adheres to the newly developed policies.

4. Implementation Support
- Guidance Throughout Implementation: Our consultants provide hands-on support during the implementation of your ISMS, ensuring all processes are followed correctly.
- Change Management: We help manage the cultural shift within your organization, promoting awareness and commitment to security initiatives.
- Resource Allocation: We assist in determining the necessary resources and tools needed for effective implementation.

5. Control Measurement
- Establishing Key Performance Indicators (KPIs): We develop measurable KPIs to evaluate the effectiveness of your information security controls.
- Regular Monitoring and Review: Our team helps implement regular monitoring of controls to ensure they function effectively and adapt as necessary.
- Continuous Improvement: We foster a culture of continuous improvement by regularly reviewing controls and adapting them to changing threats.

6. Internal Audit
- Comprehensive Audit Framework: We develop a framework for internal audits to assess the effectiveness of your ISMS and ensure compliance.
- Identification of Areas for Improvement: Our audits uncover areas that require enhancement, providing actionable recommendations.

7. Management Review
- Facilitating Management Reviews: We organize and facilitate management review meetings to assess ISMS performance against objectives.
- Identifying Strategic Adjustments: Our team helps identify necessary strategic adjustments based on audit findings and performance metrics.
- Ensuring Stakeholder Engagement: We engage management and key stakeholders to ensure ongoing commitment and support for the ISMS.

8. External Certification Support
- Preparation for Certification: We guide you through the steps necessary to prepare for ISO 27001 certification, ensuring compliance with all requirements.
- Mock Audits: Our team conducts mock audits to assess readiness and provide feedback before the official certification audit.
- Post-Certification Support: We offer ongoing support after certification to maintain compliance and adapt to evolving security challenges.
Take the first step towards a more secure future for your organization. Contact Us today, and let us help you navigate the path to ISO 27001 certification with confidence!